Online safety basics | Onlinesim
- Nov 29, 2022, 1:02 PM
- 10 minutes
Internet safety and anonymity are like the rules of the road. Nothing is complicated, but knowing and understanding how the Internet works is crucial. Otherwise, neither disabling cookies nor using Adblock, VPN, Tor Browser, or virtual machines will make your online activities secure.
In the last article from the cybersecurity series, we will tell you about online safety rules and how to follow them.
Rule 1. Use Complex Passwords and Logins
If you have logins and passwords like "QWERTY" or "111111111", any hacker can break into your account. A secure password and login is a complex combination of numbers, uppercase and lowercase letters, and symbols. A proper password length is ten characters.
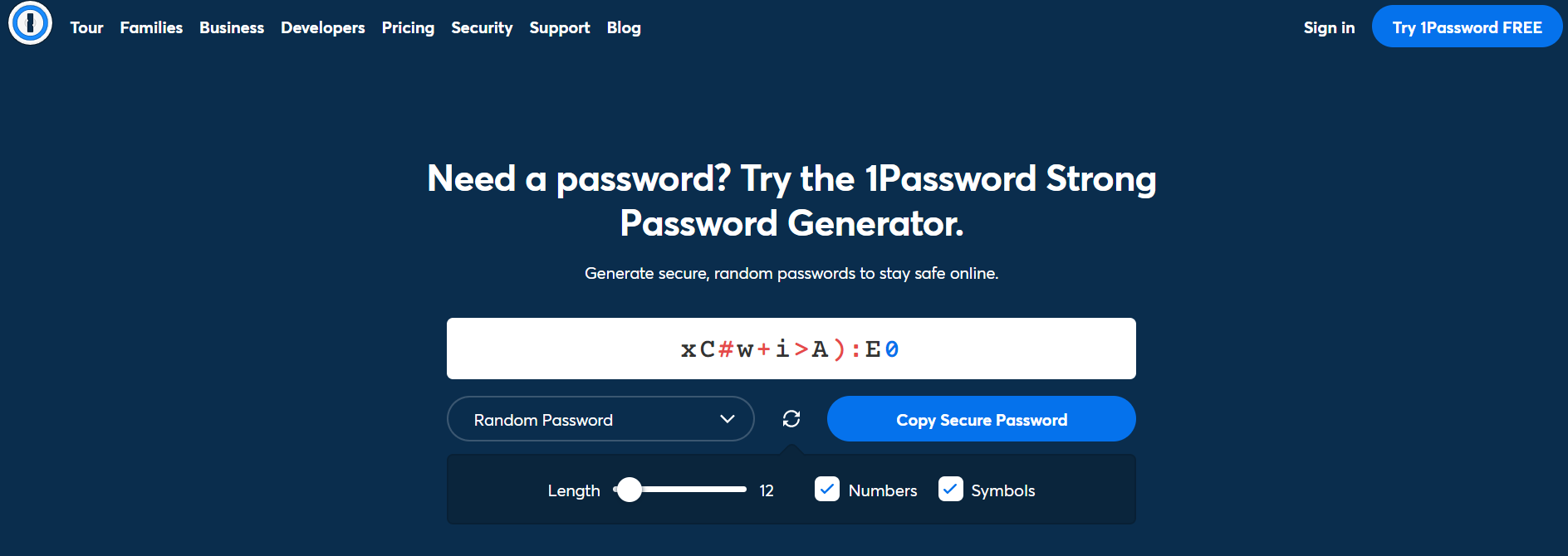
The best option is to use password generators — for example, 1Password or LastPass . You can set parameters by which a service will generate a password.
You should also use different passwords and logins for different sites.
You can set a two-factor authentication (2FA) for additional protection. 2FA is a reliable method of user identification using unique codes sent via SMS or mail.
Even if hackers steal your passwords, they will need your mail password or your phone to pass 2FA.
Rule 2. Log Out After Visiting Sites
If you sign into social networks, messengers, or other websites from other people's devices, remember to log out at the end of the session. Otherwise, others will have access to your account.
Cybercriminals can hack into your or someone else's device, which you log into, and steal your confidential information.
Rule 3. Check Internet Protocols
There are two Internet protocols: HTTP and HTTPS. It is safe to use only HTTPS websites since they use SSL or TLS encryption. Such a connection is difficult to hack, so hackers cannot intercept your traffic.
You can visit HTTP sites but only with VPN turned on. If someone tries to track you through an HTTP site, they will only see the VPN service traffic, and your real traffic will be hidden.
However, it is still possible to link a VPN address to a real person if you log in to a site without the VPN and your IP address and other data remain in the database.
You can find out more about VPNs in another article.
Rule 4. Do Not Connect to Public Wi-Fi Networks
Public networks are those found in subways, cafes, airports, and other public places. The problem with these networks is their low-security level. Hackers can break into and intercept outgoing traffic. Use public networks only using VPN or Tor.
VPNs protect all outgoing traffic, so it will be impossible to hack it. Tor uses three-layer encryption to redirect your traffic from server to server. As a result, the user's IP and location are changed.
Read more about the Tor browser in this article.
Rule 5. Keep Private and Business Online Spaces Separate
Keep personal and business online spaces separate to protect yourself from phishing and fraudsters. For example, use VPNs and Tor to log into your business accounts and regular connection to personal accounts. Hackers can link online activities to your identity if you log into your social networks or other websites through the secure channel you use for business activities.
Therefore, use a secure connection for work and a regular connection for social networks, messengers, etc.
Keep private and business accounts separate. It will help detect fraudsters and maintain privacy. For instance, if you receive a message related to your personality on your business account, it is most likely fraudulent.
You will need several phone numbers to create multiple accounts. Buying a SIM card is unnecessary — you can use virtual phone numbers. OnlineSim.io and other similar services offer such phone numbers.
Rule 6. Use a Fake Phone Number
When you use your actual mobile number, it goes into the website database. If hackers gain access to this database, they will get your number and spam call you. Moreover, if they link your phone number to your identity, they can find out:
- Your home address, the size of your house, and the amount of taxes you pay;
- The names of your family members;
- Your travel history;
- Bank account credentials and data for confirming payments.
Hackers can also steal your phone number using a SIM swap scam method. Basically, they transfer your phone number to another device and trick websites' security systems into believing that the scammer is you.
Hackers who steal your phone number will access your accounts, chats, financial data, and so on.
Besides, they can use your number for sending phishing SMS and robocalls. They can try to trick you into handing over valuable information or money. They can deceive your friends and family into disclosing your passwords or sending money to your compromised number.
You do not need to buy a new SIM card to protect yourself from fraud. You can just rent a phone number in OnlineSim. Choose any of the 10,000 numbers from 80 countries. The service offers reliable short and long-term rent numbers for receiving SMS that are not different from regular phone numbers.
You can use free virtual numbers for Russia, Ukraine, Kazakhstan, and European countries to try out the service.
Choose any free phone number to start using the service.
Do not use email or messengers to send personal data such as passport scans, documents, etc. If fraudsters hack into your account, they will get all this data.
Rule 7. Do Not Share Confidential Information Through Chats
If you still have to send documents, delete them right after sending them or use encrypted services. For example, Protonmail and Posteo are safe and reliable for sending emails; Telegram, Signal, and Wire are secure chat apps.
Rule 8. Limit the Information You Share on the Internet
Do not publish your phone numbers, email addresses, or other personal information. Otherwise, scammers can link online activities with a real person and use this information for social engineering.
Social engineering is the psychological manipulation of people into forcing them to perform actions or disclose personal data.
Rule 9. Do Not Click Suspicious Links
Scammers can send links that lead to phishing sites, such as fake marketplace websites. When a person follows such a link and tries to buy anything, this website steals bank card details.
Also, a phishing link can lead to malicious websites that steal data from devices. Cryptomining malware may be built into a website that launches when a person visits the site. Cryptomining slows down the user's PC performance and reduces its lifespan.
Therefore, do not click links sent by an anonymous person. Even if someone you know sent the link without an accompanying message, do not follow it. It is possible that a person's account was hacked and is being used for sending spam.
The scammers offered people to submit bids for ongoing government projects and embedded a "Bid" button which took users to a phishing website. There, they asked people to enter their Office 365 credentials. As a result, login data was stolen and used for hacker purposes.
There is still no information on the number of victims or the amount of money stolen.
If you want to open a suspicious link, use a virtual machine. A virtual machine should not contain personal information like bank card data. If this link turns out to be malicious, the virtual machine will take all the heat. You can delete it along with the virus inside.
Rule 10. Buy a New Card for Online Payments
Keep on your bank card only the amount of money you are going to spend. Even if scammers attack you, they will not steal all your savings.
Another option is to use Apple Pay or Google Pay. These services encrypt bank card details, so websites can not get access to your CVC or card number.
Rule 11. Use Antiviruses
Viruses can damage your PC and steal confidential information like passwords, user names, or bank card credentials. Install antivirus programs to prevent this, for example, Bitdefender or Norton.
They will block suspicious sites, inform about suspicious emails, and prevent you from installing malware software.
Rule 12. Use an Anonymous Search Engine
One example is DuckDuckGo — an anti-Google, as it positions itself. DuckDuckGo does not store users' IP addresses or use cookies. Search queries are the onlything the platform works with. Therefore, the search is as private as possible. Users' data does not leave their devices, and no one can track them on request.
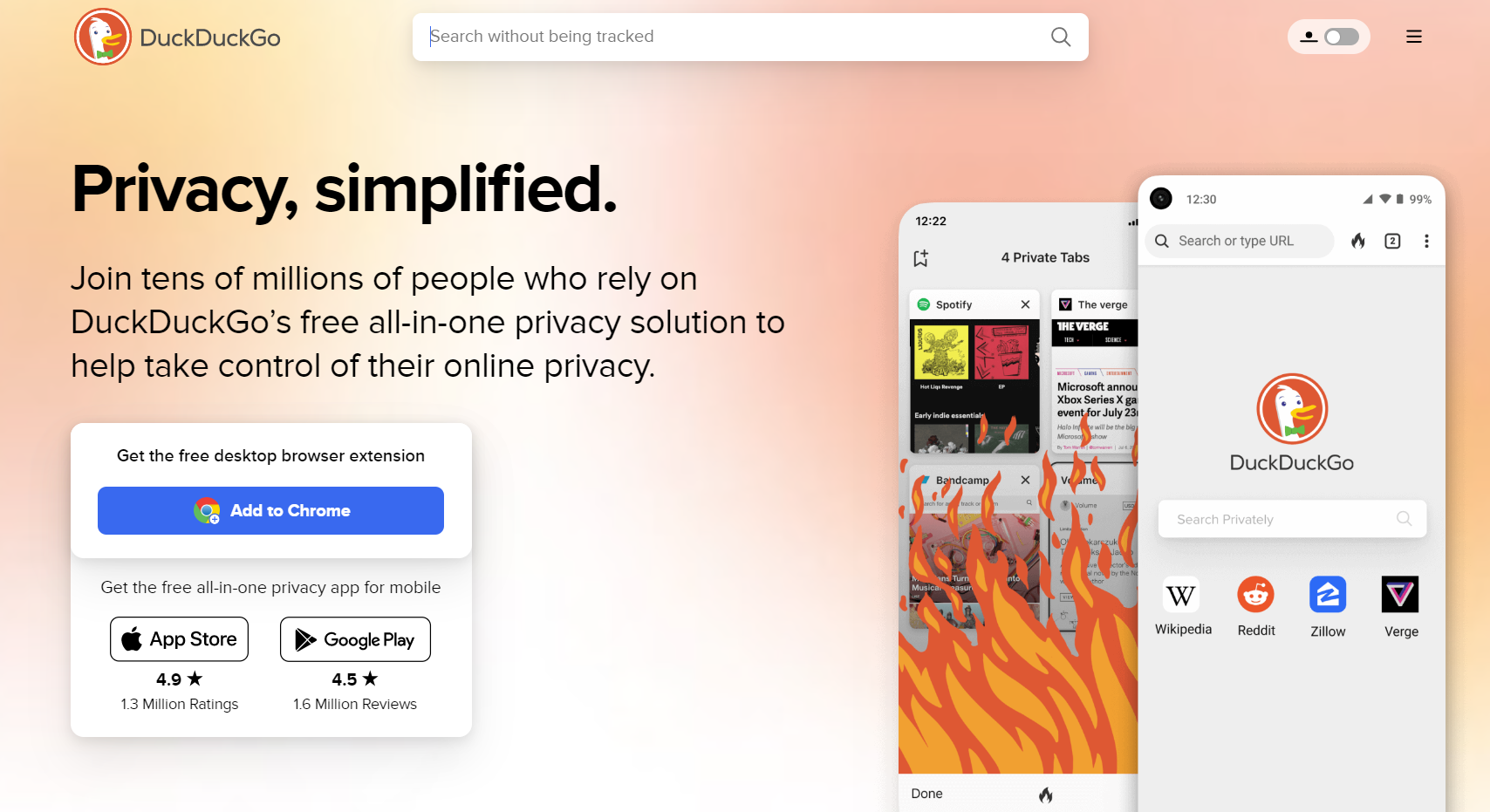
DuckDuckGo offers privacy for IOS and Android or as an extension for Google Chrome.
Secured OS for Advanced Users
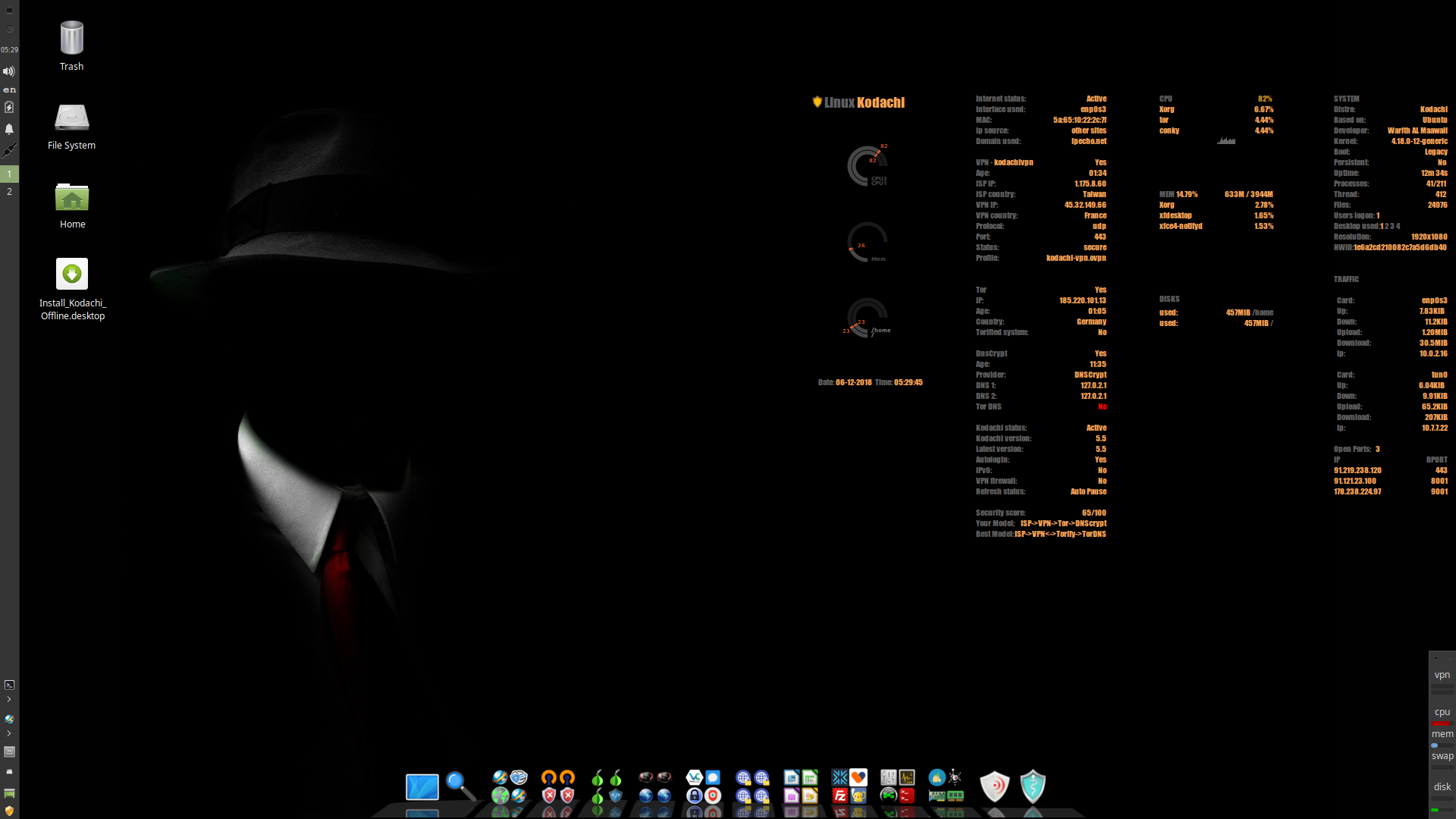
If you want greater privacy and avoid leaving any traces across the web, use a secured OS such as Talis OS, Whonix, or Linux Kodachi.
They do not necessarily need to be your primary operational systems. You can install them as a virtual machine and use two OSs simultaneously.
Their advantage is that the traffic goes through the Tor network, and all downloaded files, browsing history, etc., are deleted after shutting down or restarting the computer.
Tails OS is a Debian-based Linux distribution aimed at maintaining privacy and anonymity. All outgoing traffic gets wrapped in the Tor encryption layers; non-anonymous traffic gets blocked.
Tails start only from external media; installing it on your hard drive is impossible.
Tails is mainly used for quick access to the network, connecting to remote web sources, communicating over an encrypted channel through pre-installed messengers, and working with cryptocurrencies and files.
Whonix is a Debian-based Linux distribution that provides anonymity using VirtualBox and Tor. Neither malware nor compromised superuser accounts can lead to IP addresses and DNS leaks. All system software is configured to work with maximum security settings.
Whonix consists of two virtual machines: the Whonix-Gateway and the Whonix-Workstation. They are connected through an isolated network. One is routed all traffic through Tor; the other is entirely isolated.
Whonix allows the implementation of different sequences of Tor + VPN. You can first route all the traffic through the VPN, after that through Tor, and then again through the VPN
Whonix is used to stay safe in messengers, work with different file types and download something from the internet.
Linux Kodachi is a Debian-based distribution. It sends all the traffic through the VPN and then through the Tor network with DNS encryption.
Kodachi's distinctive advantage over other OSs is that it can change exit nodes andselect a specific country usingMulti Tor. Kodachi Linux has pre-installed cryptography tools:
- TrueCrypt and VeraCrypt are used to encrypt data;
- GnuPG, Enigmail, Seahorse, and GNU Privacy Guard Assistant are used for safe communication;
- MAT, Nepomuk Cleaner, Nautilus-wipe, BleachBit are used to erase traces on the internet;
- Kodachi also has a Tor-based browser for surfing the Web.
Kodachi Linux is used as a regular OS: for anonymous surfing, communication, online payments, and so on.
The best combination for online safety
The safety rules mentioned in this article do not guarantee full protection from hackers and scammers, especially if using them separately.
However, you can make the internet safer by consolidating several rules.
The first step — install a virtual machine. It creates a separate virtual environment for surfing the internet and protects your PC from viruses, even if they are already inside your system. Moreover, a VM prevents data leaks.
The second step — run a secured OS in a virtual machine. They can isolate viruses from the PC and secure your data.
The third step — install the Tor browser. It will change your IP address and encrypt your traffic.
The fourth step — install a VPN. It will create an additional layer of encryption and help you secure sensitive information.
Conclusion
Ultimately, you are responsible for your own online safety and anonymity. You should disable autofill and create separate online spaces for different purposes; otherwise, even the most secure OSs, fake numbers, or cryptocurrency will not help you avoid surveillance and hackers.
The best combination of internet safety methods is a secured OS + a virtual machine + Tor + a VPN.